Contributors to this article -“SavedAndRescued” and “Criselda Calupitan“. This is published as is, unedited. Forgive any typos or grammatical errors.
Official Statement from the REAL Criselda Calupitan: “I am being doxxed.”
It has come to my attention, last October 6, 2019, that my name and private mobile phone number and addresses, previous addresses, some wrong addresses, have been published online, and being monetized and commercialized without my consent, or permission by several extortion websites, ranging from peoplefinder sites to reputation sites. I did not create any account with any of those websites. NONE of those websites have asked for my permission. They do not have my consent.
This is a long article, go get popcorn.
There’s also a lot of false information and errors and lies that in my opinion is the predatory TRAP for anyone to click, to gather some “form of reaction” from either ME, or from anyone looking for ME, or anyone trying to dig dirt about ME.
Don’t fall for it because you will be exposing YOUR OWN details and you’ll just be their next victim.
It’s a sick, deprived business model targeting individuals through predatory “behavioral marketing”.
I have been researching this “doxxing done to me” and the more I learn, the scarier and really uglier it gets.
Once I publish this, IT WILL BE IN GOD’s HANDS, turned over to Him completely. I hope it helps others who may be looking for me on google, at least find, what CRISELDA CALUPITAN actually wrote, (that I really didn’t have to, but now compelled to – as a service to those looking for me, both friend or foe).
Now these doxxing is being done to many people, the “real private people”, the “privacy-conscious” people like me, that they (hackers, data brokers, extortion websites and scammers) have undoubtedly profiled in the latest series of data breaches, (Equifax data breach exposed the personal information of 147 million people, In the Capital One breach, 100 million people in the United States and 6 million in Canada were affected, Add to the data breach soup the Facebook breach, affected about 50 million users).
These hackers would know people who have owned properties, or those with businesses, would just be some of their perfect targets. These types of developers just create software or programs, or source codes that they hide behind a big word like “algorithm” – it’s all JUST SOFTWARE, not a god to bow down to, that the victims would be misled into thinking that they are helpless about, to just accept. WE ARE NOT SLAVES to these companies who monetize OUR OWN PRIVATE DATA. It’s just a software that can ALSO get corrupted and destroyed.
Some types of private people, would care about their “online reputation”. They would get targeted.
CRISELDA CALUPITAN’s reputation?
Do you think I really care? It’s just scary at first, because I have stalkers. But it can work both ways. Now it will be easier to TRACK who is stalking me and who is harassing me on my cellphone.
CRISELDA CALUPITAN, does not matter.
JESUS CHRIST matters.
We should not be afraid of software. I will publish here in this article, a link to the two U.S. Patents, that one website was even “invoking” as if patents gave them the RIGHT to publish personally identifiable information that they OBVIOUSLY purchased from the hackers involved in those data breaches.
In statistics, you know the “average”. But if you want to understand ANY phenomena, study the “outliers”.
The “data” of the private people will be the link to the puzzle on WHAT BIG DATA BROKER COMPANIES purchase via those types of DATA that was breached.
Because not everybody is on social media, or FB.
Not everybody publishes their cellphone numbers.
Study those people IF YOU WANT TO REALLY CATCH those responsible for these data breaches.
When these stolen data gets dumped into a humongous “people data base”, the software, then kicks in.
It’s all “aggregation, data gathering, compiling, extrapolating” – it’s like these hackers don’t care about ANY of the ACTUAL people whose lives and names and data they are trying to monetize.
It’s a sad reality, what the “evil love of money”, making money, their god, can compel people, organizations, to do these abominable things to their fellow human beings.
God allowed me to be victimized by doxxing too, for a reason that’s between God and me. And now for the internet to see. And to God IS THE GLORY!
“Lord God Almighty, Heavenly Father, Jesus Christ, Thank you for giving me this brain. Please help me with my faith, that through all these internet chaos, done against me and many others, we can proclaim YOUR goodness and protection God, because you promised you will deliver us from evil. Thank you for making me aware that this is happening. Thank you for granting me calmness and Your Peace, when I am distraught, thank you for allowing me to find all of these TRUE information, so that I can share it with those whose eyes, can SEE, and whose ears, can HEAR. Please help me fight the good fight. Please protect me, and all the other innocent victims of doxxing, in Jesus Name we all pray, Amen!”
So here we go with MY truth. Truth Finder? My life is my own. God knows my reputation. Not some websites who are defaming me or trying to extort me, or extort anybody looking for me. What if I don’t want to be found?
How did Criselda Calupitan find out she is being doxxed?
It was on October 6, 2019 that I learned that I was being doxed, when someone tried to find me and contacted my son. I was not aware of this doxing, because I don’t really google my name. No one has told me about this directly. I didn’t (and don’t) want my son being harassed by anyone that I do not want to speak with anymore – our children has to be “off limits”, if I have blocked certain people from calling my phone, they should NOT and MUST STOP HARASSING me, or my child to force me to speak to them. I don’t owe them anything. NO ONE can force me to speak to anyone that I do not want to speak with. The abusers in my past cannot harass me into speaking to them.
How can Criselda Calupitan’s Personal Details find it’s way online and published without her consent?
This is a sample of what happens when there are security breaches, or when enemies just want to continue on with their obsessive harassment on the offline world, and bringing it to the online world. It’s sad. But it’s a sad reality now.
“In September of 2017, Equifax announced a data breach that exposed the personal information of 147 million people. The company has agreed to a global settlement with the Federal Trade Commission, the Consumer Financial Protection Bureau, and 50 U.S. states and territories. The settlement includes up to $425 million to help people affected by the data breach. ” – Source: Federal Trade Commission https://www.ftc.gov/enforcement/cases-proceedings/refunds/equifax-data-breach-settlement
What will I do?
I’ll just tell the truth, MY truth.
Criselda Calupitan is being doxxed.
I have ALSO confirmed that I WAS and AM just ONE of the 147 million people affected by the Equifax security breach.
Since October 6, 2019, God has led me to people and resources who would enlighten me and pray for me in order to have the courage to COME OUT and publish this article, sharing what I have learned and researched thus far.
Getting doxxed when you have stalkers is a security and safety risk. One website even published “Criselda Calupitan’s” name plus DEATH records. (Is that a threat?)
When one is attacked like this online, human nature’s reaction would be “fight or flight.”
I can use my technical skills (I’m not boasting, I have those skills) to at least publish this article, so it ALSO shows up on Search Engines. I am just being victimized by doxxing.
Why are there so many extortion websites with Criselda Calupitan’s name on it?
I’m not the only victim of these extortion websites, where true personal details like name, cellphone number and current or old addresses are mixed with lies like you might have some criminal record or in a sex predator list. That will freak out anybody. And then they say it’s “public data”. THEY ARE LYING. If you fall for their trap and actually create an account with one website, you will give them your TRUE information, and also your Credit Card Information. And if you ask them to remove your personal data, they will ask for your U.S. Driver’s License. (Giving them more of your TRUE information, SO DON’T!).
They also have a lot of wrong information about me attached to my name – that’s for them to fix, not me. In the I.T. world, that’s called “data clean up” – I am not going to clean up what some evil hacker did to me and my name online. Mixed with some data that I will not confirm or deny. If the Equifax data breach caused other information to get sold, well, that’s for them to clean up and correct too. People are not made up of credit reports, or credit scores. It’s not even a reflection of who we really are. Who we really are, is who we are before God.
Welcome to the new technological warfare, that GOD WILL WIN. There must be Christ followers who will “fight the good fight” and inform as many people as we can, to BE AWARE, of all this commercial surveillance that is done on EVERYONE on the internet. Experts are speaking out and coming out in Congressional Hearings (I will embed the videos in this article), because it is becoming SO VERY INTRUSIVE and DANGEROUS. All of us are affected.
After researching this, I found out that these types of people finder websites are using the same servers. The owners of those sites sure love to protect their own privacy because they hide behind their web hosting company.
One website was invoking two U.S. Patents that I ended up studying those too.
You can read them yourself, to see how they trap and extort people. There are laws against spam (misuse of email addresses). They are drawing from a contact list from a database. What they are doing now is, instead of sending email from the same contact database, they are now mixing with lies on a website template, and then publishing it online instead. And then scaring their victims into extortion.
They create accounts without permission, then publishing the lies in their attempt to scam and extort people.
Even if you ask them to remove your data in one website (which you just actually confirmed, if you tried to click the “Is this you, fix your data” links), your corrected data will pop up and get updated in another website. It will be a never ending monthly subscription charged to your credit card. Don’t fall for that trap. It’s a software pulling information from the same contact database. Read the U.S. patents. This must be what the Data Broker industry’s way of collecting, and then aggregating all of the U.S. Based individuals’ personal data, a piece of data here and there, and then one security breach after another, well, READ AND STUDY what the source code and invention does, so you will see.
DO NOT ALLOW all of these “apps” on your phone, or other “interconnected” devices dumb us down.
Before you purchase ANYTHING, ask yourself, do I really NEED to buy this? Or did I just see advertisements about this over and over and over again, until I got curious to the point of checking it out, and then actually BUYING it?
You’ve just been closely hyper-targeted via behavioral marketing which is predatory.
NOW, it’s all just software. You are being victimized without you even being aware. READ this article and then WATCH the Congressional hearings below.
IF YOU ARE MADE AWARE, then you will make YOUR OWN informed decisions, and NOT because you got put and hypnotized into a “BUYING or SPENDING” trance!
Interesting U.S. Patents 6,701,348 and 6,694,353
They are patented U.S. inventions. An Intellectual Property. Go check out what it can do.
U.S. Patent No. 6,701,348 – Method and system for automatically updating contact information within a contact database
Abstract
A method is proposed for automatically updating and maintaining contact information for various contacts stored in a contact database without requiring an individual to manually update their contacts by using an automated reply process for the maintaining of contact information, as well as only requiring one individual to be a member of the service. Updating of the contacts with the automated reply process installed is more frequent.FIELD OF THE INVENTION
This invention relates to a method of updating, maintaining and verifying contact information for various contacts held in a database and more particularly to an automated method of maintaining the contact information fields within a contact database without requiring an individual to manually update same.
Read more at the SOURCE – U.S. PATENT OFFICE WEBSITE:
[US Patent & Trademark Office, Patent Full Text and Image Database] – Direct Link: http://patft.uspto.gov/netacgi/nph-Parser?Sect1=PTO1&Sect2=HITOFF&d=PALL&p=1&u=%2Fnetahtml%2FPTO%2Fsrchnum.htm&r=1&f=G&l=50&s1=6,701,348.PN.&OS=PN/6,701,348&RS=PN/6,701,348
And this is the direct full link to the document, with images that would explain how the contact details are automatically processed:
So you see, the automation, the “invention”, cannot just hide behind big words like Artificial Intelligence, AI, Big Data, Internet of Things that people should just accept hook line and sinker, that we can’t do anything about.
Surely, the inventor saw the need for it, to be used for automatically updating a user’s contact details in his database, but it would be under the presumption that it IS the user trying to update their own data.
Surely, the benefit this gives to companies using this patented invention is great for those who want it.
Now imagine being forced into cleaning up somebody else’s act of harvesting or data mining your personal information, without your consent, and they mix and merge databases, and then expecting you to clean it up, provided that you pay for it?
Isn’t that a tad bit deceptive and predatory? Especially if the data falls into the wrong hands like evil hackers?
What if these types of websites are just using these U.S. Patents to provide some type of legitimacy to the doxxing that they do?
And then here’s another U.S. Patent that one of the extortion website has put on the footer of their website, God knows if the inventors even know how their invention is being abused like this and negatively affecting people whose data are now exposed without the consent of those affected individuals:
U.S. Patent No. 6,694,353 – Method and system for automatically updating electronic mail address information within an electronic mail address database
ABSTRACT:
A method is proposed for automatically updating and maintaining email contact information for various contacts stored in a contact database within or outside of an email application without requiring an individual to manually verify and update email addresses. The method flags an invalid email address of a destination individual when an error message is received indicative of mail delivery failure. Another available email address of the destination individual is then automatically designated as their primary address.
FIELD OF THE INVENTION:
This invention relates to a method of updating, maintaining and verifying electronic mail (email) address information for various contacts stored in a database.
Read more at the SOURCE – U.S. PATENT OFFICE WEBSITE: http://patft.uspto.gov/netacgi/nph-Parser?Sect1=PTO1&Sect2=HITOFF&d=PALL&p=1&u=%2Fnetahtml%2FPTO%2Fsrchnum.htm&r=1&f=G&l=50&s1=6,694,353.PN.&OS=PN/6,694,353&RS=PN/6,694,353
And here’s the direct link to the Full pdf Document, with images of what the software does:
So you can understand, the Technology is there, but how is it NOW being used?
WATCH AND LISTEN TO THE EXPERTS IN THE FOLLOWING VIDEOS AND BE AWARE:
“Marketing of Consumer Information” – DECEMBER 18, 2013
“A representative from the Federal Trade Commission, private industry officials, and privacy advocates testified on the impact to consumers the collection and marketing of personal information by the data broker industry. The Senate Commerce Committee had released a staff report that day on the practices of the industry showing that data brokers, effectively unregulated, were collecting a huge volume of detailed personal information including things such as medical, financial, and legal concerns that were categorized and sold.” – DECEMBER 18, 2013
Source: https://www.c-span.org/video/?316852-1/marketing-consumer-information
“Technology Companies and Algorithms” – JUNE 25, 2019
“The Senate Commerce Committee held a hearing to examine how technology companies use algorithms and machine learning to influence the public. Witnesses included industry scholars and professionals who offered insight into companies, such as Google, YouTube, and Facebook.”
Source : https://www.c-span.org/video/?462071-1/technology-companies-algorithms
Universal Language, Babel, Confusion
1 “Now the whole earth used the same language and the same words.
2 It came about as they journeyed east, that they found a plain in the land of Shinar and settled there.
3 They said to one another, “Come, let us make bricks and burn them thoroughly.” And they used brick for stone, and they used tar for mortar.
4 They said, “Come, let us build for ourselves a city, and a tower whose top will reach into heaven, and let us make for ourselves a name, otherwise we will be scattered abroad over the face of the whole earth.”
5 The Lord came down to see the city and the tower which the sons of men had built.
6 The Lord said, “Behold, they are one people, and they all have the same language. And this is what they began to do, and now nothing which they purpose to do will be impossible for them.
7 Come, let Us go down and there confuse their language, so that they will not understand one another’s speech.”
8 So the Lord scattered them abroad from there over the face of the whole earth; and they stopped building the city.
9 Therefore its name was called Babel, because there the Lord confused the language of the whole earth; and from there the Lord scattered them abroad over the face of the whole earth.” – Genesis 11:1-9
“Social Media and Content Monitoring” – JUNE 26, 2019
Executives from Facebook, Twitter and Google testified on Capitol Hill about efforts to counter online terror content, hate speech, and misinformation on their platforms. The social media officials all agreed on the importance of prohibiting online terror content and recognized their commitment to free speech. They also discussed company actions involving foreign interference in U.S. elections, a manipulated video of House Speaker Nancy Pelosi (D-CA) and the Facebook Live stream of the mosque shootings in Christchurch, New Zealand. Nadine Strossen, a New York Law School professor, also testified.
Source: https://www.c-span.org/video/?462052-1/social-media-content-monitoring&start=92111
“Internet and Consumer Protection” – OCTOBER 16, 2019
“Google and Reddit officials testified before two House Energy and Commerce subcommittees regarding the internet and consumer protection. A focus of the hearing centered on Section 230 of the Communications Decency Act which protects internet service providers, tech companies and internet users who re-post third-party material against liability.”
Source: https://www.c-span.org/video/?465331-1/google-reddit-officials-testify-internet-consumer-protection
“House Judiciary Subcommittee Hearing on Online Data and Privacy” – OCTOBER 18, 2019
A House Judiciary subcommittee held a hearing on how online platforms such as Google and Facebook use consumers’ personal data to target advertising and for other economic purposes. Among the witnesses testifying were former Obama administration Council of Economic Adviser Chair Jason Furman and Rohit Chopra, commissioner of the Federal Trade Commission (FTC). Witnesses discussed competition in the digital economy, consumer privacy, and data portability among online platforms.
Source: https://www.c-span.org/video/?465453-1/house-judiciary-subcommittee-hearing-online-data-privacy
“If my people, which are called by My Name, shall humble themselves, and pray, and seek My Face, and turn from their wicked ways; then will I hear from heaven, and will forgive their sin, and will heal their land.” – GOD. – 2 Chronicles 7:14 (KJV)
Below are just some of the laws that I have found, the extortion websites that allege that it is “public data” are actually lying, because there are LAWS that specifically protect private data, when these same private data is BREACHED though, oh well, God help ALL OF US!:
1. There’s a lot of sensitive personal health information data which is supposed to be PROTECTED by HIPAA, protecting or covering email transmissions.
“To the extent the information in this e-mail and any attachments contain any protected health information as defined by the Health Insurance Portability and Accountability Act of 1996 (“HIPAA”), PL 104-191; 45 CFR Parts 160 and 164; or Chapter 181, Texas Health and Safety Code, it is confidential and/or privileged. This e-mail may also be confidential and/or privileged under Texas law. The e-mail is for the use of only the individual or entity named above. If you are not the intended recipient, or any authorized representative of the intended recipient, you are hereby notified that any review, dissemination or copying of this e-mail and its attachments is strictly prohibited.”
2. GDPR? (General Data Protection Act). ALL Websites must comply to that, to protect people’s privacy, and their right to be forgotten.
3. The most frequently quoted statement by a Supreme Court justice on the subject of privacy comes in Justice Brandeis’s dissent in Olmstead v. U. S. (1928):
“The makers of our Constitution understood the need to secure conditions favorable to the pursuit of happiness, and the protections guaranteed by this are much broader in scope, and include the right to life and an inviolate personality — the right to be left alone — the most comprehensive of rights and the right most valued by civilized men. The principle underlying the Fourth and Fifth Amendments is protection against invasions of the sanctities of a man’s home and privacies of life. This is a recognition of the significance of man’s spiritual nature, his feelings, and his intellect.”
4. Personal Information
Right of privacy: Access to personal information
The right of privacy has evolved to protect the ability of individuals to determine what sort of information about themselves is collected, and how that information is used. Most commercial websites utilize “cookies,” as well as forms, to collect information from visitors such as name, address, email, demographic info, social security number, IP address, and financial information. In many cases, this information is then provided to third parties for marketing purposes. Other entities, such as the federal government and financial institutions, also collect personal information. The threats of fraud and identity theft created by this flow of personal information have been an impetus for right of privacy legislation requiring disclosure of information collection practices, opt-out opportunities, as well as internal protections of collected information.Source: https://www.law.cornell.edu/wex/personal_Information
5. “The Gramm-Leach Bliley Act (also known as the Financial Modernization Act of 1999) establishes guidelines for the protection of personal financial information. Financial institutions are required by law (15 U.S.C. § 6803) to provide a privacy policy to customers, which explains what kinds of information are being collected and how that information is used. Such institutions are further required to develop safeguards in order to protect the information they collect from customers.”
6. “The Fair Credit Reporting Act (15 U.S.C. § 1681 et seq.) protects personal financial information collected by consumer reporting agencies. The Act limits those who can access such information, and subsequent amendments have simplified the process by which consumers can obtain and correct the information collected about themselves. The FTC also actively enforces prohibitions on fraudulently obtaining personal financial information, a crime known as “pretexting.””
“An invasion of privacy is usually only possible when there is some form of reasonable expectation that the person targeted is left alone or in a private setting when the invasion occurs.
There are four different kinds of invasion claims possible depending on the circumstances.
1) One is an intrusion of solitude which involves an incident where the victim’s intrusion is considered offensive.
2) Appropriation of name or likeness is when someone’s identity is used usually for monetary benefit without permission.
3) Public disclosure of private facts occurs when the perpetrator reveals secrets of his or her target that are not of public concern.
4) False light is the misrepresentation of a person or casting him or her in a bad light through false information.”Source: https://www.hg.org/legal-articles/what-is-an-invasion-of-privacy-claim-42450
7. Instances of Appropriation of Name or Likeness
“There are many who have taken an individual’s name or likeness in face or body for monetary or other means of benefit. This is more often observed when a company has used the name of a celebrity or his or her likeness in some type of advertisement without asking permission to do so from the individual. While many states restrict the use of this tort for only commercial use, there are some states that permit private citizens to submit claims when this occurs. There are some occurrences where someone impersonates another individual to obtain confidential or personal identifiable information. This is when the target’s privacy has been invaded. Because the individual’s name and likeness are treated as his or her property, there are similar case details that apply to these claims.
The False Light Incidents
When someone’s public disclosure of information is misleading and may shine a false light on the individual, this crime has been committed. This means there was some form of publication, it was reckless and it painted the victim negatively in a manner that is considered offensive or embarrassing. When any of these invasion of privacy crimes have occurred, it is important to contact a lawyer for assistance with litigation and resolving the matter.”
8. If you are in Texas, the Law should also protect you. So if they say they are compiling information they found from “public data” – provide the direct link!
(4) requiring that the state agency’s Internet site be credited as the source of information reproduced from the site and requiring that the date that the material was reproduced from the site be clearly stated;
(6) specifying other policies necessary to protect from public disclosure personal information submitted by a member of the public to a state agency’s Internet site to the extent the information is:
(A) confidential;
(B) excepted from the requirements of Section 552.021; or
(C) protected by other law intended to protect a person’s privacy interests.
SOURCE: https://statutes.capitol.texas.gov/SOTWDocs/GV/htm/GV.2054.htm#2054.126
9. PDF on Doxxing, Source: https://pubext.dir.texas.gov/portal/internal/resources/DocumentLibrary/OCISO%20Doxxing%20SWATing%202019.pdf
10. https://www.ic3.gov/media/2015/150421.aspx
10. Libel, Slander, Defamation
“Libel, as defined in Black’s Law Dictionary, is “any publication that is injurious to the reputation of another.”
Slander, on the other hand, is the “speaking of base and defamatory words tending to prejudice another in his reputation, office, trade, business, or means of livelihood.” Thus, libel is written defamation; slander is spoken.” – Douglas Lee
Source: https://mtsu.edu/first-amendment/article/997/libel-and-slander
Doxxing is not a joke. It can put doxxers in jail.
“New York Man Sentenced To 24 Months in Prison For Internet Offenses, Including “Doxing,” “Swatting,” Making a False Bomb Threat, and Cyber-Stalking
“…committed the doxing and swatting to entertain themselves, to exact revenge for official conduct they found objectionable, to express animus toward certain victims, and for their own notoriety. ”
What do others say about how to recover from doxxing?
We really have to remember, the “online world”, is not the “real world”. Most Data Scientists really work behind the scenes. It’s sad also when I read an article about an Epidemiologist getting doxxed – I mean, really, doxxers should leave people alone, those who are doing something good for the benefit of humanity. There are a lot of women techies who are pushed too far, there are others who just gave up the internet altogether, some have even gotten so stressed out to the point of suicide.
Doxxing is not just an online attack, it’s an emotional and psychological attack too. And for what? Money? Revenge? Hatred? Can anyone live through the guilt when they find out their victim got killed by their stalker?
I am publishing this because people with stalkers have that “cloud of fear”. Victims of an assault will always have that “cloud of fear”. Do businesses have ANY RIGHT to be targeting those people too? What’s the point of causing another human being that additional stress?
The comment below was from a 2015 Article, How Do I Recover From Doxxing? I was googling “Doxxing Laws” and it was one of the websites that came up. I didn’t realize at first, how “common” doxxing was. But we need to realize that getting victimized by doxxing is not the end of the world, it’s hurtful, yes, but it is ONLY in the online world:
“Well, your first mistake was trying to live on the web, a “place” that does not really exist. The internet is a great thing for communication and to go looking for information, but there is really no reason for most people to have a “web presence” and people who do not (like 99.99% of all people in human history) do not end up with these sorts of totally artificial and unnecessary problems.
Your first question therefore should be: “why do I care?” followed shortly after by “what does it REALLY matter?”
People who actually know me know what I am like and no amount of online dirt about me would convince them otherwise. People who do not know me could be easily convinced to believe anything about me they might find online – but they do not matter to me; since I do not know them I do not care if they know me or if they imagine they know me. I do not know the internet reputations of any of the people I deal with in the real world, I do however care very much about their actual reputations in the real world and I know who I can trust on their word or a handshake.
This silly mental disorder of the Twitter generation that thinks that an online reputation or identity matters at all need to seriously contemplate what really matters in life and need to remember that NOBODY on Earth in all of human history even had an online reputation before about 20 years ago. In most places, the people you actually need to interact with in the real world care nothing about your internet identity/presence.”
Source: https://ask.slashdot.org/story/15/09/20/0445218/ask-slashdot-how-do-i-recover-from-doxxing
Our life is our own business.
“THE CONSEQUENCES OF A FREE WEB?
We wanted an internet free from oversight, an environment where ideas could be exchanged freely. In many important ways, the web has achieved that idyllic vision. Individuals have the ability to communicate with large audiences, a power that in the past belonged only to media tycoons and governments. A lack of gatekeepers means frictionless communication, but it also means the quality of that communication can’t be controlled. And too often on the internet today, no consequence means no class. The internet experience is being degraded by those bent on settling scores, intimidating enemies, or simply silencing those with whom they disagree. The social networks say they’re powerless to stop it. Police say they’re overwhelmed. For these reasons, many people find the web a hostile and dangerous environment.Danielle Citron, a law professor at the University of Maryland, lays out some of the numbers in her upcoming book, Hatred 3.0. Citron writes that the US National Violence Against Women Survey reports 60 percent of cyberstalking victims are women. A group called Working to Halt Online Abuse studied 3,787 cases of cyberharassment, and found that 72.5 percent were female, 22.5 percent were male and 5 percent unknown. A study of Internet Relay Chat showed male users receive only four abusive or threatening messages for every 100 received by women.”
Source: https://www.theverge.com/2013/9/12/4693710/the-end-of-kindness-weev-and-the-cult-of-the-angry-young-man
After I started a Bible app project for a Digital Ministry, all sorts of major heart pounding, mind boggling distractions have come up, from all different places, personal, professional, health-wise …
Here’s a sample of spammer attempts at trying to hack into THAT God protected website:
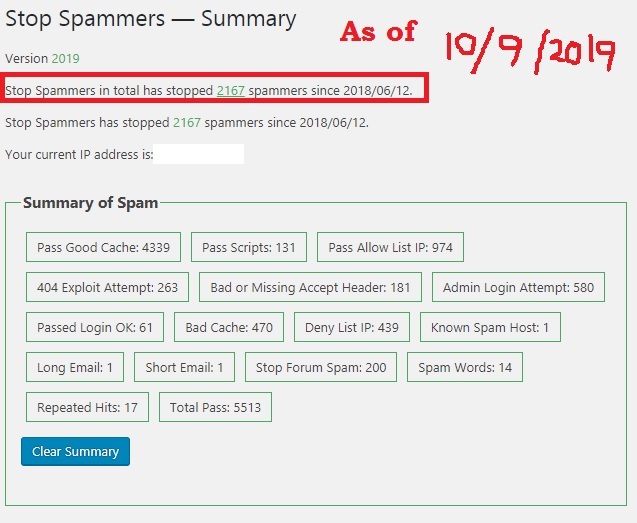
Summary Of 2167 Spammer Attempts, as of 10/9/2019
They have not succeeded. I hope they READ the bible chapters that are already published and some of the articles I wrote that I learned along the way, on that portal. Maybe God, if it is in His Will, can break their hardened hearts and open themselves up to the Truth in God’s word that we are trying to finish up in that website.
The devil’s attempt at distracting the Lead Developer of the project.
“Dox her!”
Destroy my reputation and my name?
The things that I do in Jesus’ Name is indestructible, sorry.
My reputation and my name, who cares about my reputation, or my name?
I’m invisible and irrelevant to and in this world.
I don’t matter anymore, Jesus matters.
I, Criselda Calupitan, am only publishing this article so that the good people looking for me or googling me, won’t fall for the trap of those extortion websites.
As for my enemies? I am also warning you, you will end up wasting your money and exposing yourself too on those extortion websites if you become a “registered member” of those portals because they will not honor any of your requests for refunds, and YOU TOO, will have those types of damning “lies” published about you as those extortion websites don’t care about any of us, you will also have your name loaded up on their wicked website templates. Don’t feed that beast, (You can go to websites like ripoffreport dot com, then type the website name, or google those website’s name and then add “reviews” to your search and see how MANY people they have victimized with their scam). They are defaming people. They are scaring people into revealing their own credit card information and victimizing themselves too. And the people they might be looking for.
Don’t fall for it. Don’t let your hatred or your curiosity about me or others lead you down that wrong path. You will get ensnared and hurt yourself too. Don’t do it.
I know the Truth about me, Criselda Calupitan. Ask me directly, what do you want to know, and why do you want to know, and I will tell you. I AM the authority about ME, so ask me. Nobody else knows me better than ME.
People who just love and are obsessed at judging me, lying about me, bearing false witness against me, stealing from me, I am just telling the truth that I am being victimized by doxxing. These are the very people who are master manipulators and gaslighters, that they actually even try to confuse their own victims. When you know the Truth, it’s easy to spot the lies.
What did Jesus say about that?
1 “Do not judge so that you will not be judged.
2 For in the way you judge, you will be judged; and by your standard of measure, it will be measured to you.
3 Why do you look at the speck that is in your brother’s eye,
but do not notice the log that is in your own eye?
4 Or how can you say to your brother,
‘Let me take the speck out of your eye,’
and behold, the log is in your own eye?
5 You hypocrite, first take the log out of your own eye,
and then you will see clearly to take the speck out of your brother’s eye.“ – Matthew 7:1-5 (NASB)
Christ followers should WORK on taking the logs OUT of our own eyes so that we can see clearly in order to take the speck out of other’s people’s eyes!
I am not perfect and I still have a lot of logs to take out of my own eyes, but the people who victimize me? Those who judge me because they think they know me better than I do?
WATCH how God punishes these victimizers, from this day forward, UNTIL THEY STOP, repent, and ask for God’s forgiveness for causing THIS MUCH DAMAGE and PAIN to just ONE of God’s children. God’s sovereignty rules over ALL, there is no mocking God. Whether people believe in God or not, He IS. And His Word stands. It’s the Truth:
“You shall not wrong a stranger or oppress him, for you were strangers in the land of Egypt. You shall not afflict any widow or orphan. If you afflict him at all, and if he does cry out to Me, I will surely hear his cry; and My anger will be kindled, and I will kill you with the sword, and your wives shall become widows and your children fatherless.” – Exodus 22:21-24 (NASB)
And I’ve cried buckets of tears already.
If there’s a 20 foot tidal wave coming at you and you say, “I don’t believe in tidal waves.”, do you think your unbelief of tidal waves won’t affect you?
God is watching you, me, everyone. “And His sovereignty rules over ALL.”, whether people believe Him or not.
“Thou shall not bear false witness. Thou shall not steal.” – God.
There are acquaintances for a reason, there are friends for a season, and there are friends for a lifetime.
And this life is so short, all we have are moments.
Moments to help others, or moments that may have hurt others because of our own ignorance.
Repent. Apologize. And change for the better! Don’t hurt other people anymore!
God always helped me through all those, so I can also help others know that GOD helped me through them all, because in my past, God also sent Christians, other individuals, God sent them my way to plant those seeds of encouragement, compassion and kindness and guidance to help me, because they have also overcome, in order to see the truth – good or bad – so that I can make my own informed decision going forward.
Acquaintances or some relatives who have abused me in my past?
I cut ties with them. I don’t and shouldn’t condone or put up with evil.
People are only born “into” a certain type of family. But each of us are separate individuals.
If I was born inside a garage, that does not make me a car.
Jesus taught:
“12 “In everything, therefore, treat people the same way you want them to treat you, for this is the Law and the Prophets.” – Matthew 7:12
Christians are not doormats or punching bags.
Each one of us have our own mission in life. And often, God’s assignment for us is to respond to and help people whose pain we feel. Because we went through it.
Jesus said “If your eyes causes you to sin, gouge it out, if your hand causes you to sin, chop it off.”
It is a metaphor, we need our eyes, or our hands, integral parts of our body. If Jesus can use such an analogy, it is to impress upon us how God hates sin. Because sin is a trap and keeps people in bondage to it.
Toxic relationships that causes you to sin, like the sin of anger, of fear, of unforgiveness, of greed?
CHOP IT OFF. Cut it out. Cut and cut clean.
Most of the things people fear these days will not happen but it just leads to them doing things out of desperation.
26 “Therefore do not fear them, for there is nothing concealed that will not be revealed, or hidden that will not be known.
27 What I tell you in the darkness, speak in the light; and what you hear whispered in your ear, proclaim upon the housetops.
28 Do not fear those who kill the body but are unable to kill the soul; but rather fear Him who is able to destroy both soul and body in hell.
29 Are not two sparrows sold for a cent? And yet not one of them will fall to the ground apart from your Father.
30 But the very hairs of your head are all numbered.
31 So do not fear; you are more valuable than many sparrows.
32 “Therefore everyone who confesses Me before men, I will also confess him before My Father who is in heaven.
33 But whoever denies Me before men, I will also deny him before My Father who is in heaven.” – Matthew 10:26-33
Computers are tools for humans.
But humans are NOT computers.
Humans are not some data fields. Or data sets.
Social Media has given rise to all different uses – some use it for the good, some for the bad.
You want to know the Truth about me?
I am NOT a criminal.
I am NOT a sex offender.
I am a follower of Jesus Christ.
Jesus Christ is MY LORD AND SAVIOR.
“Jesus said to him, “I am The Way, and The Truth, and The Life; no one comes to the Father but through Me. “- John 14:6 (NASB)
Those companies that monetize my name are bearing false witness against me, and other people, in their alluding to having “dirt on people”. The people behind these companies, those that allow this, those organizations that are complicit and turning a blind eye on this type of evil inflicted against people who the government have vowed to protect, these extortionist websites are stealing from their victims and are deceiving others when they publish lies about their victims. God’s wrath is already upon these people’s head.
“Evil propagates when good people do NOTHING. So do something, if you even consider yourself good.”
These people behind those extortion websites know what they are doing. From one techie to another, I know exactly what those people are doing.
Ask any web developer who work with e-commerce sites, who have actual products to sell online. Compare it to those extortion websites, who have made the “Name, Telephone Number” of people AS THEIR PRODUCTS!
It’s easy to SEE, when you are no longer afraid to look at it, for the UGLY truth that it is. They are spreading and monetizing LIES about people.
These extortion websites TRY TO DECEIVE AND SCARE their victims into divulging their credit card information to them so that THEIR NAME used as a product, without permission , in those types of websites.
Inventors can have patents on their physical products and they can go after websites who sell these patented products. What should be illegal in the offline world, should be illegal in the online world.
If it is illegal to steal or stalk in the offline world, it should also be illegal to do that in the online world.
These extortion companies and “data miners”, from the spiritual standpoint, I don’t know if they even realize the demonic and dark influences that move them to do what they do to hurt other people, in their quest for money.
I don’t do well with extortion reputation websites who prey upon people’s stolen identities or data through hacking. I’ve just dealt and have suffered through that before, and unfortunately, those who suffer, remember. And I have not forgotten the lessons I learned from all that.
There was a time that I was NOT searchable on google, or any search engines. So now I know that this only came about because of the Security Breaches.
These evil hackers, don’t just sell your email or your passwords. They steal your privacy and your peace of mind.
These extortion websites turned lies into a depraved technology business model. These people can’t think and discern right from wrong. Liars would only believe lies and cannot distinguish what is TRUE, because there is no Truth in them.
Why do I know this, for sure?
Jesus said so:
42 Jesus said to them,
“If God were your Father, you would love Me, for I proceeded forth and have come from God, for I have not even come on My own initiative, but He sent Me.
43 Why do you not understand what I am saying? It is because you cannot hear My word.
44 You are of your father the devil, and you want to do the desires of your father. He was a murderer from the beginning, and does not stand in the truth because there is no truth in him. Whenever he speaks a lie, he speaks from his own nature, for he is a liar and the father of lies.
45 But because I speak the truth, you do not believe Me.
46 Which one of you convicts Me of sin? If I speak truth, why do you not believe Me?
47 He who is of God hears the words of God; for this reason you do not hear them, because you are not of God.” – John 8:42-47 – The Truth (Jesus) will make you free.
They can see, but cannot perceive, cannot distinguish between true or false. These are the types who find it difficult to give others the benefit of the doubt.
14 In their case the prophecy of Isaiah is being fulfilled, which says,
‘You will keep on hearing, but will not understand;
You will keep on seeing, but will not perceive;
15 For the heart of this people has become dull,
With their ears they scarcely hear,
And they have closed their eyes,
Otherwise they would see with their eyes,
Hear with their ears,
And understand with their heart and return,
And I would heal them.’ – Matthew 10:14-15 – The Meaning of Discipleship
Jesus Christ, help me.
These evil people do not care for the damage they can actually cause the name and reputation and the safety and security of people.
My Christian friend advised to publish an article about this. To tell my story and my truth and how I found out about this. One company has already been sued in the past, and I’ve researched and found two other video news, with victims also, as angry and disgruntled and appalled at this company’s audacity to rate a person’s life. But you have to pay for it, to “learn more details” so they can earn more from you.
Extortion. Blackmail. Fear. Anger. Feeling stuck. Trap. Debt. Enslavement. DEMONIC.
They bear false witness against their victims, and then monetize the lies, for those “who can’t see through” the deceptive business practice, and then you provide them your information, and then you pay them monthly to keep and publish your personal information. And if you want them to remove YOUR personal details, you have to scan your U.S. Driver’s License and send it to them.
HUWATTTTT?????
Manipulation through deception. Driven by greed for their company’s love of money. At whatever cost. Their victims would give them money in fear that if anybody googles them, and sees those lies, others would believe it.
I even saw several websites who are paying Google Ads on my name. (That by the way, is against Google Ads’ Terms of Service).
It’s that type of evil that the apostle Paul talked about in the Book of Romans:
28 And just as they did not see fit to acknowledge God any longer, God gave them over to a depraved mind, to do those things which are not proper,
29 being filled with all unrighteousness, wickedness, greed, evil; full of envy, murder, strife, deceit, malice; they are gossips,
30 slanderers, haters of God, insolent, arrogant, boastful, inventors of evil, disobedient to parents,
31 without understanding, untrustworthy, unloving, unmerciful;
32 and although they know the ordinance of God, that those who practice such things are worthy of death, they not only do the same, but also give hearty approval to those who practice them.” – Romans 1:28-32 – Unbelief and Its Consequences
Those who don’t believe and follow Christ gets punished with a “depraved mind” that they can no longer distinguish or discern between good and evil, right from wrong.
For these types of people, they will be better off being reported to the authorities so justice is served, and also reported to those who have the power to shut down these websites, and hold the website owners, and their webhosting companies accountable.
It will be interesting for law enforcement to ask, “where did these extortion websites buy that private person’s data?” (data brokers). And then ask the data brokers, “where did you buy that private person’s data?” (hackers involved in the data breaches).
In statistics, “study the outliers. NOT the average data stolen”. Not EVERYBODY exposes their own data on social media sites. Those are the outliers. The piece of the puzzle, if they really wanted to find out WHO is responsible.
Fines are not enough because it only incentivizes the stealing, buying and selling of people’s private data. There are “technical trails” and “money trails” that they can use to find these identity thieves.
16 Therefore do not let what is for you a good thing be spoken of as evil;” Romans 14:16 – Principles of Conscience
NOBODY, NO COMPANY or WEBSITE has ANY legal right or authority to publish online anybody’s name, email address, telephone number, address and then monetize it. It’s called Personally Identifiable Information (PII) and it is NOT public data and therefore cannot be used for commercial purposes, trying to extort money from me, or from anybody looking for me. They are exposing individuals to further harm and cause distress and hurt in their hearts. They’re opening a can of worms and they are putting God’s wrath on themselves.
God commanded, “Thou shall not bear false witness” and “Thou shall not steal.”
Doxxing is a Weapon of Mass Defamation. God help us.
“Dear Father God, thank you for Your strength and for giving me courage to publish this article. Please help me, and the other victims of doxing, I pray dear Father that the government officials, whom You have appointed to head over Your people, One Nation Under God, to do the right thing, to succeed and catch these forces of evil in people, that justice be done. Dear Heavenly Father, You are a God of love, yes, but You are also a God of Justice. Thank you for lifting me out of this evil attack, thank you for lifting me out of the initial shock of finding out that this type of evil is being done against me, thank you for lifting me out and saving me once again away from the spirits of fear and anger. Thank you for your clarity. I serve a God of clarity and not a god of confusion. You did not give Your Children the spirit of timidity, but the spirit of boldness to speak, to act in defense of helpless people. When I feel helpless, You give me hope. In all my weakness, Your strength is made perfect. Without You, I am nothing. Thank you for your protection. Deliver me from this evil, in Jesus Name I pray, Amen.” – Cadette Corporal Criselda Calupitan
Related Article Excerpts and Videos:
1) What is Doxing?
According to Wikipedia:
Doxing or doxxing (from dox, abbreviation of documents) is the Internet-based practice of researching and broadcasting private or identifying information (especially personally identifying information) about an individual or organization.
The methods employed to acquire this information include searching publicly available databases and social media websites (like Facebook), hacking, and social engineering. It is closely related to Internet vigilantism and hacktivism.
Doxing may be carried out for various reasons, including to aid law enforcement, business analysis, risk analytics, extortion, coercion, inflicting harm, harassment, online shaming, and vigilante versions of justice.
And from another source:
“Doxing“ is a legal term that means revealing “documents” about a person. This can range from revealing the name of a person who uses an alias, but more commonly refers to revealing whatever the person doing it feels will harm, shame, humiliate, endanger, or put the person at some risk. Doxing is a form of stalking or threatening and is illegal under many different federal and state laws, depending on the exact facts and location.
Revealing a “name” per se’ may, or may not be considered “Doxing” depending on the level of anticipated anonymity. However, in this law, the term “restricted personal information” means, “with respect to an individual, the Social Security number, the home address, home phone number, mobile phone number, personal email, or home fax number of, and identifiable to, that individual.” This is an important distinction to remember.
Once you outline the address or location of a person, within which a person can be placed at risk, YOU have VIOLATED THE LAW. PERIOD.
In all cases if you outline the physical location of any individual with the intent to harm, shame, stalk, humiliate, endanger, or otherwise compromise the safety and security of ANY individual you have placed that person in a position of risk and you are in violation of ALL State Stalking laws.
THIS is the most commonly crossed line.
…
I CAN FIND THOSE PIECES OF INFORMATION USING GOOGLE SEARCH. IS THAT STILL RESTRICTED? YES. It is illegal to announce or disseminate or post those listed pieces of information for the purposes listed in the law (18 USC § 119). Those are purposes such as threatening or intimidating or making it so others can harass or harm the person. This law is about acts that endanger the safety of or encourage attacks against a person or a person’s family. It is not about where you found the information.
READ THAT AGAIN:
This law is about acts that endanger the safety of, or encourage attacks against, a person or a person’s family. It is not about where you found the information.
18 USC § 119
The information may or may not even be on the internet; that is not a factor for a charge. A criminal act does not need to be physically possible for a charge to exist with regard to it. The activity can take the form of cyber-space and internet posting.
Doxing might also be part of a conspiracy to harm, endanger, or even kill a person. Even if unintentionally if the action of the party is intended to threaten, harass or harm.
Doxing is always illegal, whether it is done against a federal employee, a state employee, or a regular person. There are federal and state laws that specifically address doxing government employees 18 U.S.C. Sec 371 (18 U.S.C. Sec 119).
With regular non-governmental citizens, doxing falls under various state criminal laws, such as stalking, cyber stalking, harassment, threats, and other such laws, depending on the state.
Since these doxing threats and activities are made on the internet, the law of any state may be invoked, though most often an investigator will look to the state in which the person making the threat is located, if this is known, or the state in which the victim is situated.
A state prosecutor can only prosecute violations of the laws of his or her own state, and of acts that extend into their state.
However, when acts are on the internet, they extend into all the states. Thereby allowing the victim to choose the state of filing which may, or may not, be the state of residence for the victim(s) or perpetrator(s).
Increasingly with internet use, attorneys are affirming representation to the state with the strongest current legal remedies for Doxing, Cyber-Stalking, or Harassment.
…
If you are doxing a non-government person, this can be illegal under various laws that have names such as stalking, cyber stalking, cyber-bullying, harassment, invasion of privacy, threatening, terroristic threatening, endangering the safety of, intentional infliction of emotional distress (this can be a crime or a tort, depending on state law), threatening a witness (if the person is a witness), intimidation, and other laws that exist in the different states.
Depending on the situation, it might also be a hate crime or a violation of civil rights. Some states also have laws that specifically apply to students harassing or being harassed. Many states now have laws about posting a person’s name or photo on an indecent or incendiary website without their permission. It really depends on the situation, but there are plenty of laws that can be invoked and multiple remedies available.
When you do something on the internet, it reaches into every state and you open yourself up to potentially being prosecuted under the laws of any state.
Think about only using a name, it is probably a violation of law, but maybe not. However, once you go beyond the name IT IS ALWAYS A VIOLATION OF LAW.
If we are hosting a site discussion and publicly name a private party, depending on intent, there is no harm. However, if we further provide, or a commentator provides an address for the party – and we do not delete the information in a timely manner, then depending on circumstance we could be in direct violation of law.”
3) “Do Not Call Registry”
My Cellphone number has been in the “Do Not Call Registry” for many years, and the government imposes BIG fines to those companies who call those numbers. LEGITIMATE and ETHICAL companies here in the U.S. respect and follow that, or else, they pay a big fine. SO NO, my cellphone is NOT public data. Those websites who published my cellphone are LYING.
“What’s the penalty for companies that illegally call numbers on the Registry?
Companies that illegally call numbers on the National Do Not Call Registry or place an illegal robocall can currently be fined up to $42,530 per call.
The number from my caller ID was faked. Why should I report it?
Technology has made it easy for scammers to fake or “spoof” caller ID information, so the number you’re reporting might not be the caller’s real number. But in some instances, the FTC and other law enforcement agencies can still trace the call based on the information you provide. The complaint also helps because the FTC analyzes complaint data and trends to identify illegal callers based on calling patterns. We also use additional information you report, like any number you’re told to call back, to track down scammers.”
Source: https://www.consumer.ftc.gov/articles/0108-national-do-not-call-registry
4) Security Breaches
There was a security breach at the Capital One bank which had my mobile phone number.
There was also an Equifax security breach. Linkedin, yahoo and at&t (they use yahoo servers).
“In September of 2017, Equifax announced a data breach that exposed the personal information of 147 million people. The company has agreed to a global settlement with the Federal Trade Commission, the Consumer Financial Protection Bureau, and 50 U.S. states and territories. The settlement includes up to $425 million to help people affected by the data breach. ” – Source: Federal Trade Commission https://www.ftc.gov/enforcement/cases-proceedings/refunds/equifax-data-breach-settlement
I am ONE of the 147 million people affected by this data breach. Now, there are those extortion websites trying to extort money from me or from anyone who might google my name, and they say “it’s public data”.
“The Drivers Privacy Protection Act allows states to distribute personal information only to law enforcement officials, courts, government agencies, private investigators, insurance underwriters, and similar businesses — but not for direct marketing and other uses.” – Federal Trade Commission (FTC)
https://www.consumer.ftc.gov/articles/0262-stopping-unsolicited-mail-phone-calls-and-email
My mobile number, got added to the “damning” “agitating” website template that these people finder websites are conning and duping people into paying up to keep their information private.
It is NOT public data.
So with the patented software that I cited above, if you “validate” one field in one website (that draws information from a database) – all it does is either “tag” that field and make it invisible, and replace it with the latest updated data in the field. It just adds another row in your personal file – and more information gets added to your dossier.
If you open the U.S. Patent document in the link above – you will see diagrams on how the source codes work. Be informed.
If your personal information gets mixed with falsehoods, false information, then you end up suffering through the confusion and fear because you are being maligned online, never fear – don’t create profiles on those extortion websites!
If you delete your profile in one site, it will pop up in another. READ the U,S, Patent document that I have linked to above. You are just feeding the beast. Don’t fall for it.
Go check the Federal Trade Commission website to see if YOU are one of the statistic, Criselda Calupitan is one of the statistic, whose private information got breached and compromised.
“In September of 2017, Equifax announced a data breach that exposed the personal information of 147 million people. The company has agreed to a global settlement with the Federal Trade Commission, the Consumer Financial Protection Bureau, and 50 U.S. states and territories. The settlement includes up to $425 million to help people affected by the data breach. ” – Source: Federal Trade Commission https://www.ftc.gov/enforcement/cases-proceedings/refunds/equifax-data-breach-settlement
I was NOT informed about the Equifax breach. The only time I learned about it was after I have researched and pieced everything together, after now learning that I have been doxxed. Several days ago. After someone was trying to see if I can shell out 100,000. And then maybe 20,000. NOPE. Not falling for it. I can see and sense and discern through the deception.
‘Do not fear, for I am with you; Do not anxiously look about you, for I am your God. I will strengthen you, surely I will help you, Surely I will uphold you with My righteous right Hand.’
– GOD (Isaiah 41:10 NASB)“If my people, which are called by My Name, shall humble themselves, and pray, and seek My Face, and turn from their wicked ways; then will I hear from heaven, and will forgive their sin, and will heal their land.” – GOD. – 2 Chronicles 7:14 (KJV)
We have the Philosophy of Liberty that we can all remember, too.
“When Criselda Calupitan got hacked in 2017, someone told her about a good message, courtesy of youtube, but it was in Italian. It was by the head of the catholic church, Pope Francis, a good message that applies to everyone.
So she recorded her own translation of the message – (We only just need to take an honest inventory of our strengths, and our gifts. Our weakness? Don’t focus on that. We all have our own weaknesses. But we also have something good in and about each and every one of us. Just focus on what is good. Focus on God)
Just use your God given gifts for the good. No one is perfect, but we can all try.” – “SavedAndRescued“.
“And some wise guy said this – “We accumulate fans, followers, subscribers, and visitors to websites as if those are worthwhile metrics to measure the quality of our lives. We compare our lives to the highlight reels of everyone else’s, prioritizing attention over connection, and vanity over value. But the only metric that’s worth measuring your life with is time well spent. Helping other people is always, in God’s eyes, time well spent.”
I am opening the comment section on this article. You can leave a comment if you want.
The people who matter to me and the organizations that I am connected with know how to reach me via an end-to-end encryption private messaging app (look at it at Signal dot org – call me via that. The publicized hacked email addresses that these extortion websites have published? Do not use those anymore. Contact me through Signal or call me straight so you know it is ME you are speaking with. I even learned recently that at least 6 of my relatives voicemails are being redirected to some other voicemail accounts – God knows where. Had I not been able to see it for myself and got the “screenshots”, for evidence. It brought me to tears. There really is EVIL in people who are behind their use and abuse of technology. All these doxxing empowers evil people and stalkers and bullies.
Just watch how GOD PROTECTS HIS CHILDREN. All of these types of evil bad news came to my knowledge without me having to do anything.
Maybe it’s time to buy a brick mobile phone. Maybe it’s time to just use CASH again.
Thank you for reading all of this. God bless you and your family.
Peace on earth. And prayerfully, peace on the internet!
Criselda Calupitan
P.S. This article is “purposefully long-winded”, and some paragraphs “redundant”. It’s an SEO strategy so it will show up on organic search results when people type the keyword “Criselda Calupitan”.
Jesus Christ, thank you for rescuing me once again! TO GOD BE THE GLORY!
“I can do all things, through Christ, who strengthens me!” – Philippians 4:13
To clear your browsing data: PRESS: The “Control + Shift + Delete” keys simultaneously on your keyboard, in order to remove cookies from your browser that might have been stored for viewing the videos on this page, and from reading this page, in addition to the other cookies on your device.
This website Calupitan.com has cookies from PHP and WordPress.
Third party cookies on this specific page, come from c-span, google, and the video player that streams the video. (I block third party cookies on my devices).
Make it a habit to clear your cookies by clicking “Control + Shift + Delete”.
“Individuals are permitted to use C-SPAN video coverage of federal government events on a non-commercial public Internet site so long as C-SPAN is attributed as the source of the video.” – https://www.c-span.org/about/copyrightsAndLicensing/
Thank you! Now let’s move on along! 🙂 Turn on the Search engine visibility for this website so it can get crawled (even with just this one substantive blog post. (Also remember to leave the threaded layout by 2 layers only). I appreciate all the HELP and PRAYERS! 🙂
I activated the “5 minute comment editing timer”.
Grateful! \o/
The comments got automatically closed after a week. I reopened it! =)
I am just noting it here, two of the (many) portals that I am a Systems Administrator of, got hacked two days ago. Guess what the two sites were? One site was for my personal ministry, and the other was for my bible app project. These two sites, there were no Personally Identifiable Information (PII) that was compromised since me being a favorite target of some hackers (God knows who they are), I have my own security systems in place, so all they can do is try. I was the only one that they hacked. So what did they do? They changed the database name into something else, so that when anyone types the site, it will show an “Error connecting to the database”. Right. Because there was an intrusion that changed it. Well, those two sites are back UP and running. Thanks to Arun also for helping out. These webhosting companies also have their own staff and tech people that hopefully would protect the sites in their servers. In technology, there is a trail to almost everything. And they are logged. So, I will just add these notes/comments here of stuff like that that I know are related to all these data breaches. I would have to MANUALLY do separate “clean installations” of CMS (Content Management Systems), because there are “auto installations” or “one click installations” that can REALLY mess up a website when the automatic updates overwrites whatever customizations have been done on the site. For this specific website, I installed a generic WP and just used also a generic WP theme. I will update the theme with a WP theme I created or developed myself, since the only updates on that is the one I will also develop. Since I created it, there were/are no updates necessary, since it is still working. “If it ain’t broke, don’t fix it.”. I am changing the Theme for this website because while I was doing the other forum post which had MANY pictures and videos, I crashed this site twice! There are restrictions on the sizes of files I can upload, and I just feel safer about the theme that I myself built and tweaked since there are just too many malwares these days. It really is agitating. So I am changing the WP theme here to the one I developed. I would have to change the WP theme name to “CriseldaCalupitan” as advised by one of my techie friends. It will be an additional “tag” or “keyword” in the tech side of things to beat those who are doxxing me, in the search engines. When I attended my son’s event at his school, it dawned on me, as one of the speakers was talking about “personal branding”. I have dragged my son to all the many conferences I would have to attend in the past, because it was just him and me, and so I know about “personal branding” or “branding” – but on the internet? I’d much rather be incognito these days, however, if there are hackers and people monetizing my name, using my name even, and running google ads on it, these days, well, I will make them pay google MORE money, because I will just make the “keyword” or the “tag” much more expensive for them to be paying. So hit them back and beat them at their own game. There’s no way in hell I will get extorted into paying them so they will remove my name from their website. It will get removed, when they realize they are paying google ads way too much for running ads on the name of a “nobody” like me. 🙂 Also, it is against googleads Terms of Service to be “monetizing” or running ads on ANY person’s name. What kind of horrible person would do that? Right? Well, there’s so much evil on the internet, the good techie people should rise back up when they are targeted. And write something – document whatever it is that is being done to them online. I spoke to a police officer at church about this doxxing because it’s scary to be “SWATTED” – you can google that and how these types of evil doxxers do not care about people nor respect Police Officers’ time by making false reporting. It’s not joke and like I wrote – all these types of activities ARE tracked. So, just choose to do the RIGHT thing. But now this site is looking like one big old “Criselda Calupitan” link. Still, it’s an SEO strategy and will just be found by those who know the direct link to the site. After checking, right now, this website is ranking at the Top 1,121,624 of websites worldwide (according to Alexa Dot com) so my strategy of writing this BIG and LONG blog post last October, is gaining some traction with it only having a “shell” of a website. With just 1 substantive blog post, and 3 other almost empty blog posts. Watch how the ranks go higher as I add more content. If I decide to. 🙂
Also, thanks to Pastor Alan, Pastor James, GayeT for praying with and for me through all these doxxing and tech chaos, as we seek Godly wisdom in what to do against this type of evil done to me and my son. I also thank LilibethD, GraceD, GraceO, MarciaD, MennieP, NickM, MartinS, SavedAndRescued, TonyP, and other techies who have shared personal experiences and strategies with me that God allowed, so that the anxiety brought about by this horrible attack on my privacy has raised. Now, I will go back to the other portals I need to work on. 🙂
ALSO, if you are a victim of doxxing, just do what I did – get your own Dot Com, and then document that you are being victimized, so that the timestamps on the article that you publish will appear too when anybody searches for your name on the internet. Posting the information on social media is not enough (Search Engines do not crawl social media posts, so if you want it to appear on Search Engine results, you have to post your name on some website – preferably your own, that you yourself manage). The longer the article you write, the better, because you would get more organic traffic as you post “unique content”. Because there are also software that are called “article spinners” that scrape the internet and plagiarize original content (I’ve had that happen to me many times in the past when I was blogging daily for three years, under a business name, that’s how I knew about it). I had to write software to STOP these type of plagiarizers stealing my original content. I’m not going to publish a HOW TO on that. If you need help with it, you can contact me on Signal DOT org app, and I also would advise you to get a FREE encrypted email at protonmail dot com. These hackathons and snoopathons are gettting scarier by the day. But there’s hope when you are made aware of what’s going on.
I’m closing the comments here. (And opening the comments in the latest blog post here:
https://www.calupitan.com/never-mind-this-post-its-just-a-placeholder-for-my-hackers/
I’m also putting a recaptcha on logins. To many spambots trying to login.